Statistics: Posted by nwokiller — Mon Feb 04, 2013 12:30 am
]]>
Statistics: Posted by tcm1998 — Sun May 12, 2013 7:20 pm
Statistics: Posted by nwokiller — Mon Feb 04, 2013 12:30 am
Statistics: Posted by Urban Legend — Sun Feb 03, 2013 11:05 pm
Statistics: Posted by welhim — Sat Feb 02, 2013 10:56 am
Statistics: Posted by bartbilf — Sat Feb 02, 2013 1:07 am
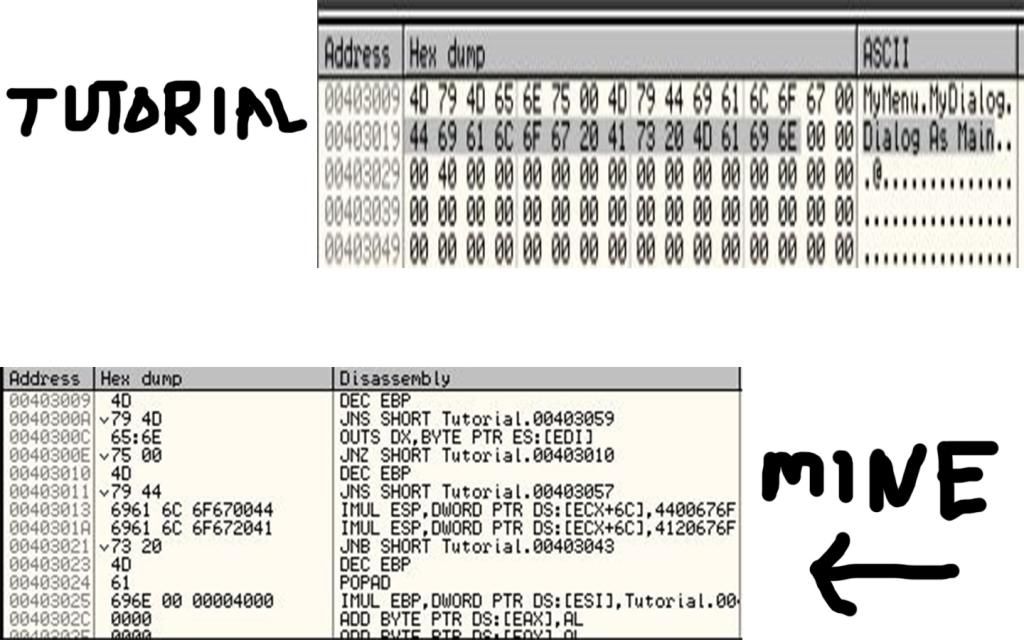
Statistics: Posted by welhim — Fri Feb 01, 2013 5:37 pm
#include <iostream>
#include <windows.h>
#include <Psapi.h>
#include <tchar.h>
#include <TlHelp32.h>
#pragma comment( lib, "psapi" )
using namespace std;
int main() {
MODULEENTRY32 me32;
int pauser,mp,newscore;
HWND hWnd;//handle to a window or form
DWORD dwID; //PID of target
DWORD baseAddress; //32 bit unsigned integer
DWORD finalAddress;
HANDLE hProcess; //handle to the process in question
HANDLE testHandle;
const char* chModName = "Solitaire.exe";
hWnd = FindWindow(NULL, "Solitaire"); //find solitaire window
GetWindowThreadProcessId(hWnd, &dwID); //get the process PID based on the Window
hProcess = OpenProcess(PROCESS_ALL_ACCESS, NULL, dwID); //open a handle to the process
cout << &hProcess << endl; //print handle to screen
testHandle = CreateToolhelp32Snapshot(TH32CS_SNAPMODULE,dwID);
Module32First(testHandle,&me32); //get first module information
baseAddress = (DWORD) me32.modBaseAddr; //set base address
baseAddress = baseAddress + 0x00097074; //add offset to get first pointer
cout << baseAddress << endl; //show pointer
ReadProcessMemory(hProcess,(LPVOID*)baseAddress,&mp,4,0); //read the target of the pointer
cout << "INITIAL ADDRESS: " << hex << mp << endl;
baseAddress = mp + 0x2C; //add 2c to the target
cout << "NEXT ADDRESS: " << hex << baseAddress << endl;
ReadProcessMemory(hProcess,(LPVOID*)baseAddress,&mp,4,0); //read next target
baseAddress = mp;
cout << "NEXT ADDRESS: " << hex << baseAddress << endl;
baseAddress = baseAddress + 0x18; //add 18 to the next pointer location
cout << "FINAL ADDRESS: " << hex << baseAddress << endl;
ReadProcessMemory(hProcess,(LPVOID*)baseAddress,&mp,4,0); //show final score
cout << "Contents of Final Address: " << mp << endl;
cout << "Write new value: " << endl;
cin >> newscore;
WriteProcessMemory(hProcess,(void*)baseAddress,&newscore,sizeof(newscore),NULL); //write new score
system("Pause");
CloseHandle(testHandle);
CloseHandle(hProcess);
return 0;
}Statistics: Posted by RageMachine — Wed Nov 14, 2012 1:34 am
Statistics: Posted by nwokiller — Tue Nov 13, 2012 11:16 pm
hWnd = FindWindow(NULL, "Solitaire"); //find solitaire window
GetWindowThreadProcessId(hWnd, &dwID); //get the process PID based on the Window
hProcess = OpenProcess(PROCESS_ALL_ACCESS, NULL, dwID); //open a handle to the process
cout << &hProcess << endl; //print handle to screen
bHandle = GetModuleHandleA(lpModuleName);
cout << &bHandle << endl;
Statistics: Posted by RageMachine — Tue Nov 13, 2012 8:27 pm
Statistics: Posted by markdeleon123 — Tue Nov 13, 2012 2:24 pm
Statistics: Posted by markdeleon123 — Tue Nov 13, 2012 5:11 am